With unleashing the full potential of IoT for the industrial edge and the trend towards data-driven decision making, the IT/OT convergence helps industries improve the overall business performance by streamlining their existing operational processes. However, such convergence increases the risk of being exposed to attack surface, since traditional OT networks, which typically operated on a standalone basis due to the machinery oriented characteristics, are now connected over the Internet or IT networks that makes OT devices, such as SCADA, HMI, RTU, and PLC much more vulnerable to cyber attack.
In order to defend OT networks against cyber attack, a multi-layered security strategic approach called defense-in-depth is recommended to protect critical OT assets. As there is no single security solution that can entirely defend all kinds of cyber attack. Therefore, by implementing a defense-in-depth strategy, the likelihood of security breach is greatly reduced. If someone manages to bypass a number of security controls in a single layer, all critical assets are still protected by the remaining security controls placed in the next security layer. This makes it difficult for someone to conduct a successful cyber attack. The defense-in-depth strategy consists of these five security layers: Physical, Network, Computer, Application, and Device. Policies, Procedures, and Awareness are used to tie all these five security layers together, since each security layer complies with predefined policies that are implemented via procedures. Lastly, awareness means how much technical know-how employees have about how to protect their networks from cyber threats
Find DIN-Rail Managed Switches and Industrial Ethernet Switches in our catalog.
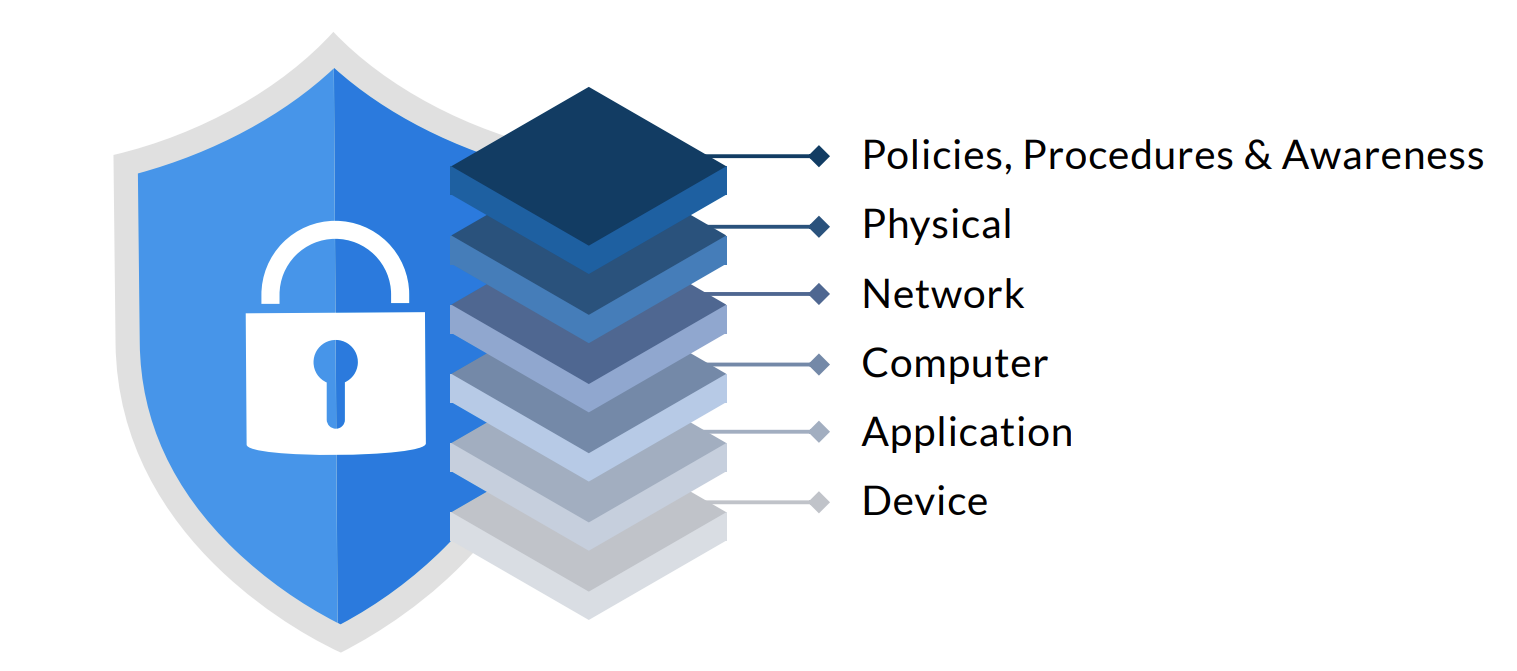
Physical Layer: Referring to physical security that keeps employees and critical assets on the premises safe from intruders. For example, the deployment of video surveillance systems and IP cameras for monitoring facilities or the use of security cards or biometrics for door access is a form of physical security
Network Layer: Referring to network security that controls users or devices access to OT networks. Some examples include implementing 802.1x port authentication for wired or wireless networks, filtering network traffic through access control lists, and planning and configuring network segmentation.
Computer Layer: Referring to the protection of SCADA workstations against system infiltration in any form by installing anti-virus software, configuring firewall, and applying OS patches on a regular basis.
Application Layer: Referring to keeping all software programs installed on SCADA workstations and operator workstations free from vulnerabilities by updating all software programs on a regular basis.
Device Layer: Referring to the process to reduce attack surface on any device, such as encrypting network communication via HTTPS or SSH, enabling login password complexity check, disabling unused ports and services, encrypting files/configurations stored on workstations/switches, and setting up system log servers.
Segmenting OT Networks
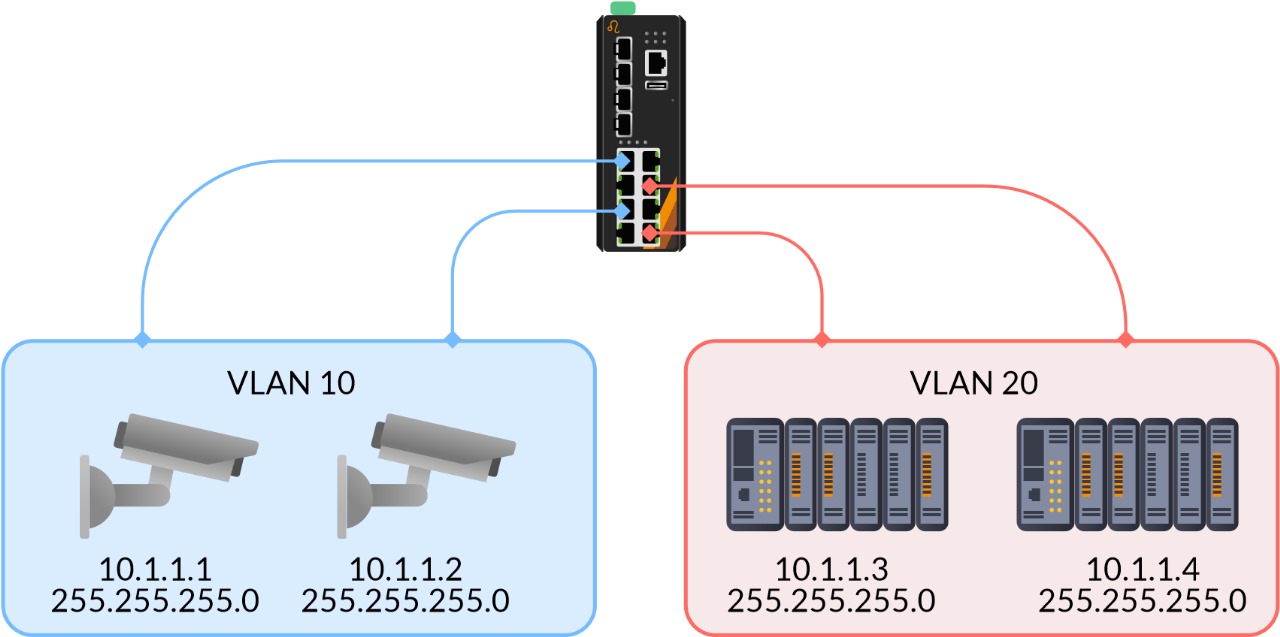
In simple terms, network segmentation involves the practice of splitting an entire physical OT network into several smaller logical networks (i.e., VLANs) that are isolated from one another to enhance network security. The main benefits of network segmentation include the separation of critical data traffic in order for protecting against interception and increasing the number of broadcast domains (i.e., each VLAN represents a broadcast domain) that eliminates the impact of unnecessary broadcast traffic generated by any failing device (i.e., unnecessary broadcast traffic will not be forwarded to any other broadcast domain).
The following scenario illustrates network segmentation. We may split our physical switch in half by creating two VLANs. To give an example, the production VLAN can be used for controlling solar panels in a field site and the surveillance VLAN can be used for monitoring onsite security. All devices in the same VLAN can communicate with each other whereas the exchange of data between two VLANs is impossible
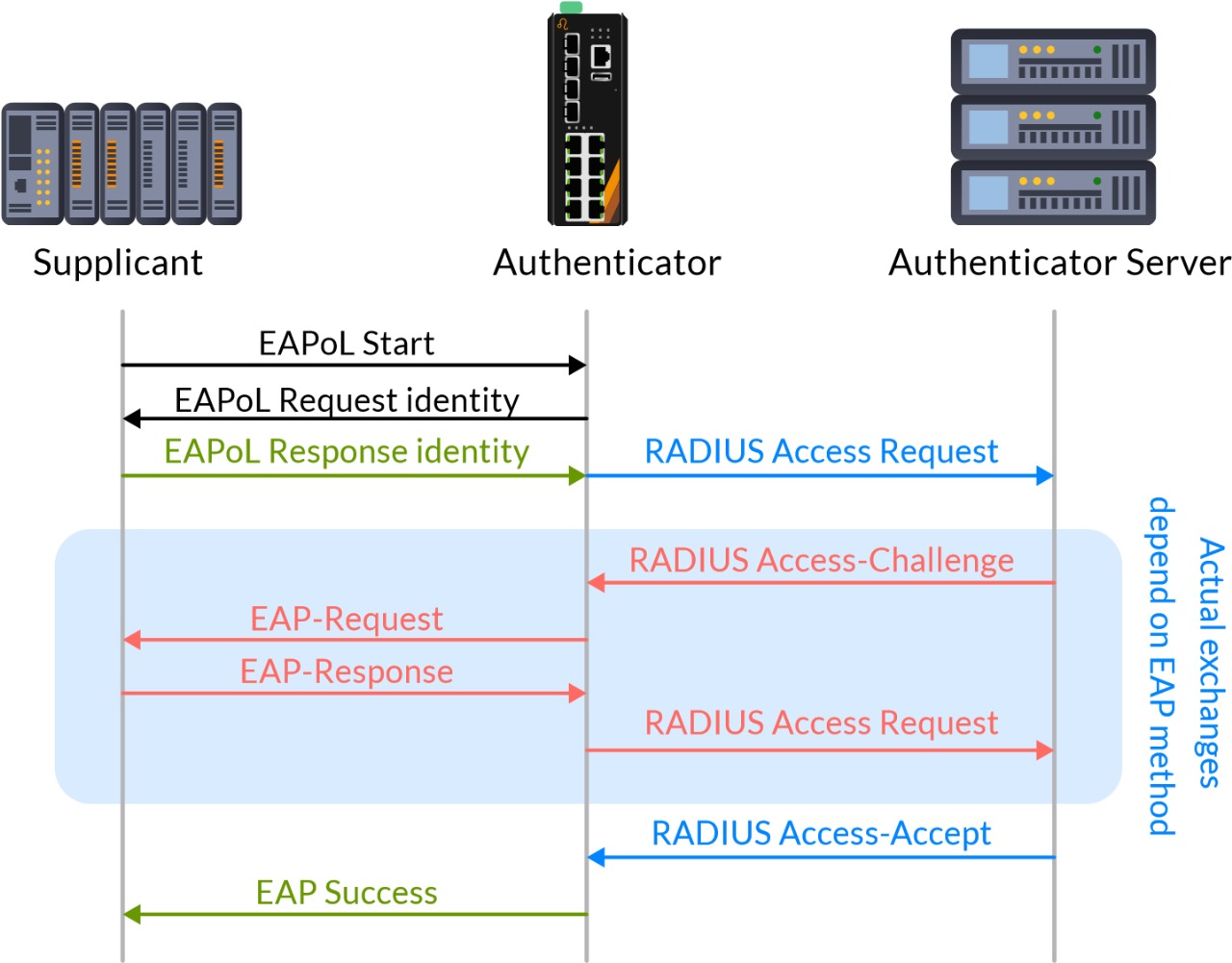
Securing The Edge of OT Networks
Automation equipment, such as PLCs for controlling and monitoring industrial operations is mostly located at the physical edge of the OT networks. There is also an increase in risk of unauthorized access to the OT networks in a scenario where someone has broken physical perimeter security and has tried to conduct cyber attacks on critical infrastructure by connecting his own equipment in order to reprogram a single PLC, causing that PLC to operate abnormally. Such attacks can result in financial loss or even loss of life. Therefore, there are two approaches to mitigating such attempts, which are IEEE 802.1X Port-Based Authentication and MAC-Based Authentication. An end device connected to an 802.1X protected switch port isn’t able to send any traffic except for EAPOL traffic to an Ethernet managed switch until the proper credentials are successfully authenticated. Two protocols i.e., Extensible Authentication Protocol over LAN (EAPOL) and Remote Authentication Dial-In User Service (RADIUS) are used during the authentication process. EAPOL is used for communications between the end device and the Ethernet managed switch, while RADIUS forwards authentication details to the RADIUS server. After the authentication process is complete, the accounting process starts to record the session time period of the connecting end device, which is often used for auditing purposes
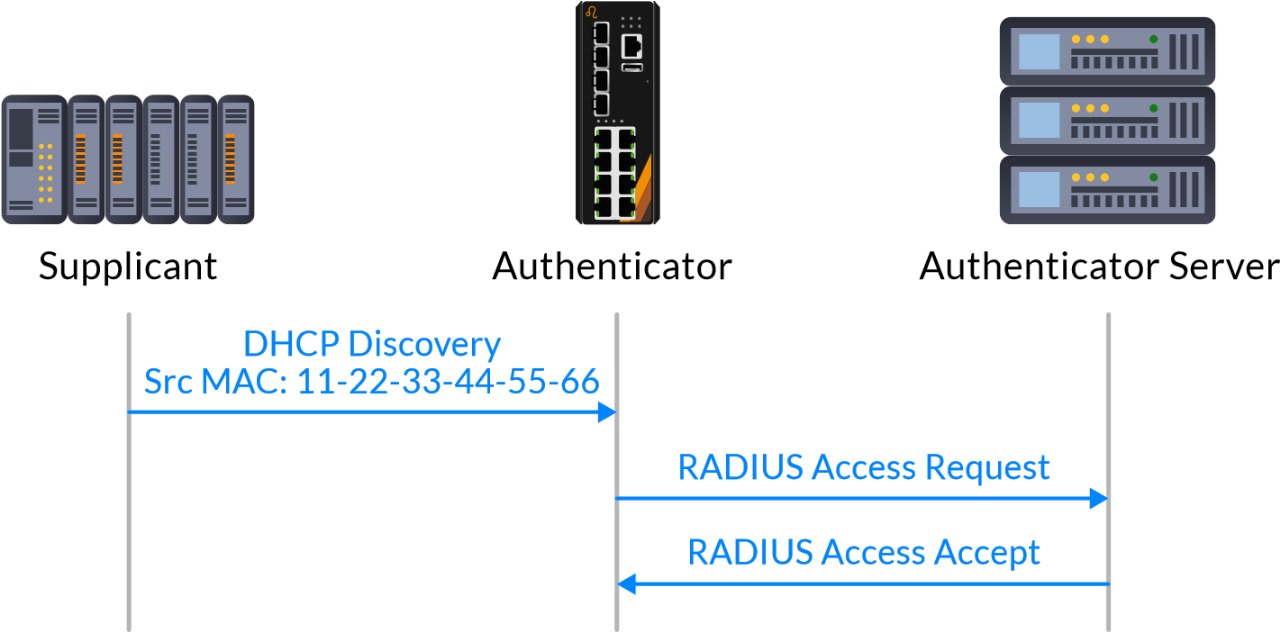
MAC-based Authentication is another alternative for authenticating end devices based on their hardware addresses. With MAC-based Authentication enabled on the switch port, the Ethernet managed switch learns the hardware address of the connecting end device through any packet, which in turn uses the learned hardware address as both username and password in the subsequent RADIUS message exchange with the RADIUS server. If both the username and password match an entry in the RADIUS Server’s database, then the RADIUS server grants the connecting end device access to the network. After the authentication process is complete, the accounting process starts to record the session time period of the connecting end device, which is often used for auditing purposes
Filtering Network Traffic via ACL
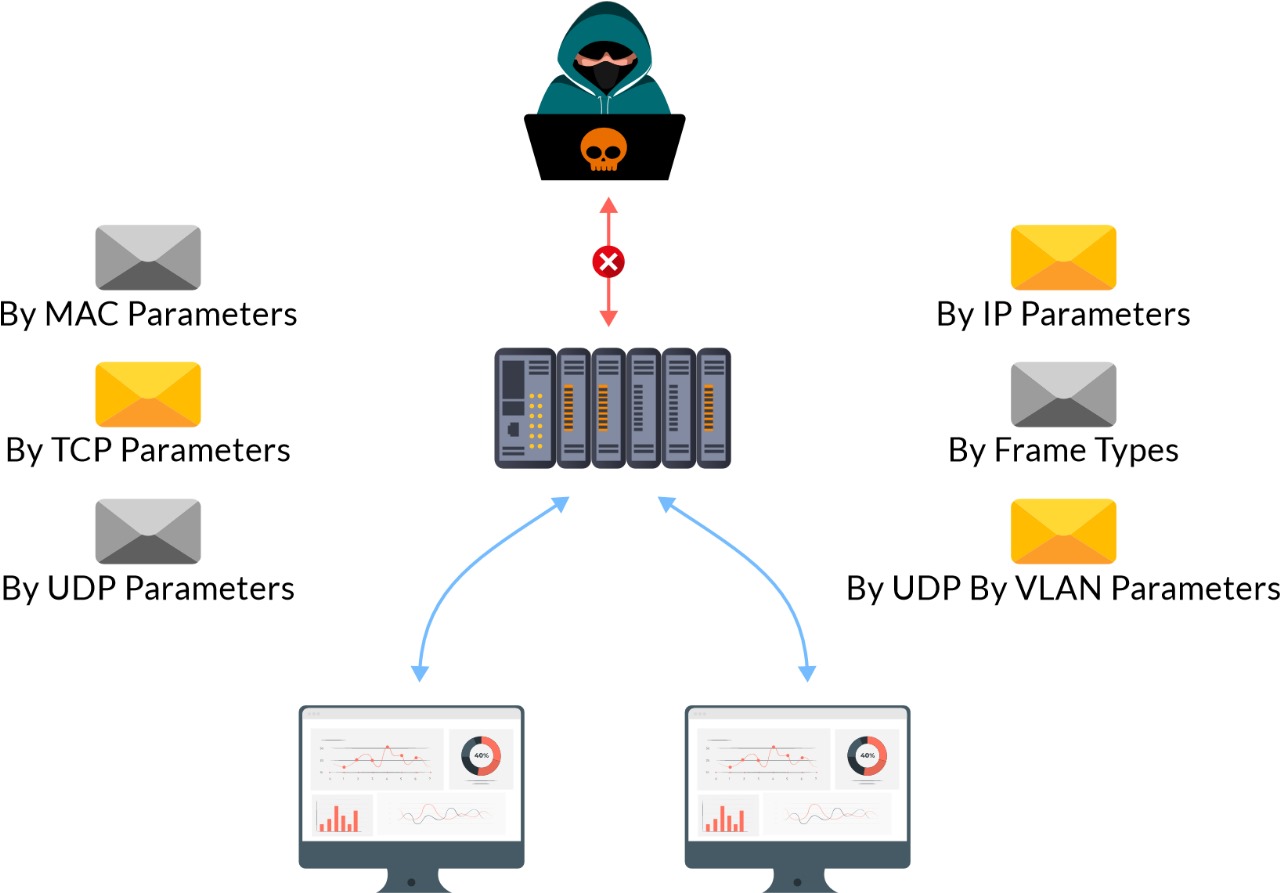
An Access Control List (ACL) is a set of security statements that defines the packet matching conditions based on the Ethernet header fields (e.g., source MAC address, destination address, VLAN ID, tag priority, and EtherType) or IP header fields (e.g., source IP address, destination IP address, protocols: icmp/tcp/udp along with port numbers). Therefore, network communications are able to be restricted to a specific group of senders and receivers. When an ACL is configured on a managed switch, the managed switch compares each incoming packet against the ACL statement one by one. If there is a match, the managed switch either permits it or denies it as defined in the statement. To give an example, if we want to allow Modbus TCP/IP traffic between a SCADA with an IP address of 172.16.0.1 and a PLC with an IP address of 172.16.0.2, then two ACL statements would need to be created for covering the bi-directional communications. The main purpose for implementing ACLs is to ensure network traffic can be trusted with non-malicious intent
Selected Products

|
ET2-0602-M |

|
ET5-0802-M |

|
EG2-0800 |

|
ET2-1600 |

|
ET2-0500 |

|
EG2-0501-SFP |

