While commercial companies apply the opportunities offered by the Internet of Things (IoT), digitalization has become a necessity for industrial enterprises as well, thus, creating a demand for the Industrial Internet of Things (IIoT). Over the recent years, digital technologies are being deeply integrated into the industrial control systems. The industrial control system networks were physically isolated and nearly immune to cyberattacks. However, the complexity of cyberattacks has evolved recently and now IT and OT (CAM) specialists have to integrate the solutions that enhance the level of industrial cybersecurity. Hence, understanding industrial cybersecurity requirements will help companies to lower the risks of cyberattacks.
Read on to find out more.
There exist two viewpoints on how the enterprise network should be arranged. As a rule, the OT engineers understand the work of industrial protocols quite well, however, they lack the informational security knowledge. On the contrary, the IT specialists possess the required competence, but do not deal with OT networks as they do not know how it works.
Accessing the problem and complying with the users’ requirements, MOXA has started to develop the cybersecurity line by actively integrating additional functions and releasing new devices that conform to industrial security requirements.
Differences between OT and IT
IT

OT

[Expertise]
— Communication with OT vendors, little knowledge of industrial security
— Communication with IT vendors, expertise in industrial security

[Position]
— ACS is protected
— Industrial security is within the responsibility of IT department
— IT department can disrupt the work of ACS, let them stay away fr om our systems
— Windows and Linux are the basic OSs in ACS
— ACS is untouched
— PLC can’t be touched as it may get broken
[Strong/
weak points]
- Large-scale systems and networks
+ Industrial devices
+ Industrial protocols
+ Large-scale systems and networks
- Industrial devices
- Industrial protocols
All cybersecurity solutions from MOXA can be divided into 3 large groups:
Device security solutions
To enhance the level of device security, MOXA has released a bunch of functions increasing cybersecurity based on the requirements of the IEC 62443 international standard. The complete set of security functions has been implemented within many devices, including Industrial Ethernet Switches, industrial routers, rack mount managed switches, rack mount unmanaged switches, switches of EDS-500E series, selected NPort models of serial interface servers and protocol gateways.
Intrusions and attacks prevention
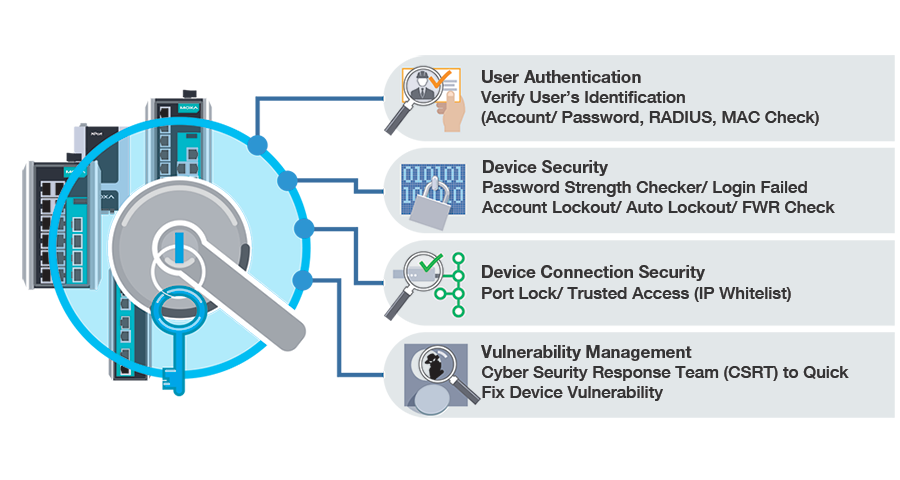
To prevent intrusions and attacks, it is important to have a good access control mechanism that can identify, authenticate and authorize users. Moxa’s network devices support functions of user account management, password policy and authentication interface that conform to technical security requirements of the IEC 62443 standard.
- Operators can use these functions to create user accounts and assign roles, grant access rights and access control rights to devices within networks.
- Authentication by means of IEEE 802.1x, RADIUS, TACACS + protocols and support of MAB (MAC Address Bypass) for devices that do not support IEEE 802.1x.
- Port security is provided with Static Lock function or its MAC-address Sticky upd ated version that allows auto learning the MAC address of the connected device without its manual typing. ACL (Assess Control List) provides network security by controlling access to devices.
- Providing protection against DoS attacks is possible by disabling unencrypted and unused interfaces (for example, HTTP and Telnet) and limiting maximum amount of login users, to prevent a device from overload with superfluous requests.
Confidential data protection
Moxa devices support the HTTPS/SSH protocol extended features that provide secure data transmission over insecure networks. In order to protect data from being stolen or corrupted, Moxa provides such functions as SNMP password encryption and network configuration encryption, that ensure the highest level of network device protection.
NPort 6000 secure interface converters use SSL for secure data transmission in Secure TCP Server, Secure TCP Client, Secure Pair Connection and Secure Real COM modes. NPort drivers conform to the SSL standards and automatically negotiate the encryption key. To prevent hacker attacks, NPort automatically switches from DES/3DES to AES encryption for highly protected data transmission.

Tracking network events
Protection against cyberattacks does not end with the devices settings only. You should constantly track the network status and check network events for potential threats. Despite the fact that it is quite difficult to detect a breach in real time, security event logs can help you find the source of the problem. Information from these data logs can be implemented to track network activity, analyze potential treats or identify devices that are improperly configured and can be later used for disconnecting user access, deleting user accounts, or device restart.

MOXA solutions
Network security solutions
Industrial control system networks used to be completely isolated from a corporate network and the Internet network. Despite the fact that more and more devices are getting connected to industrial networks, most OT operators do not comprehend the necessity of cybersecurity. Due to the amount of cyberattacks aimed at crucially important industrial sector, it is clear that the process control networks are under the high risk of attacks.
Network segmentation for zones and areas
Secure network architecture requires ACS network to be segmented into protected and isolated zones and areas. The communication between each zone and area is secured by firewalls, which additionally reduces possibility of a network to become a cyberattack victim.
Industrial network secure routers of EDR series provide protection of zones and areas by means of a firewall (Transparent Firewall) that protects control networks and critical devices such as PLC and RTU from unauthorized access. Thanks to this solution, there is no need in reconfiguring the network parameters, which makes deployment faster and easier. EDR-810 series supports Turbo Ring redundancy technology that makes network segmentation more flexible and economically efficient. Moreover, Ethernet switches from Moxa can create virtual subnets (VLAN) to divide each area into smaller networks that will isolate traffic form other VLANs.
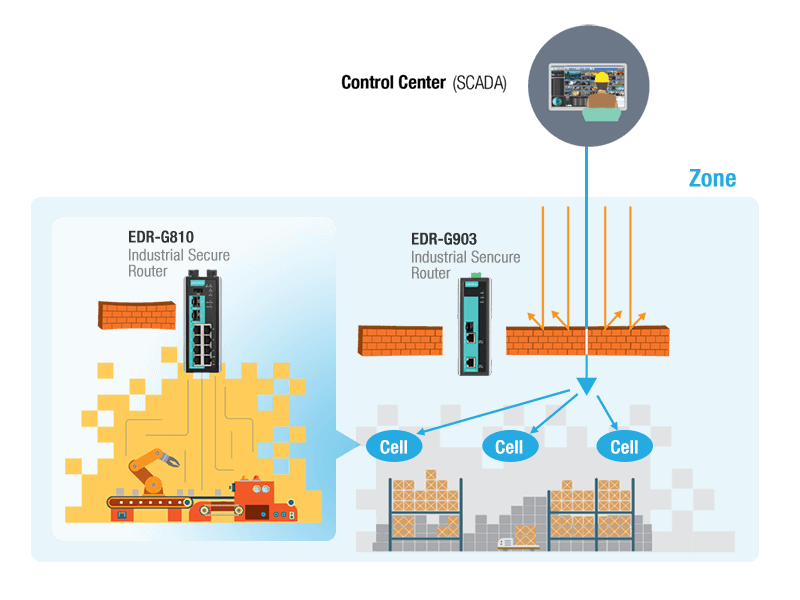
Decomposition of a network into subnets increases the security level.
Control over traffic transmitted between zones
Traffic that passes between zones within an industrial networks must be thoroughly studied, in order to enhance security. There are several ways to do that. One of the methods is exchanging data via DMZ, wh ere a data server is installed between the secure ICS network and insecure networks without a direct connection. EDR-G903 series from Moxa can help to provide secure traffic control by applying firewall user rules. The second method implies that EDR routers perform deep check of Modbus TCP packets (PacketGuard technology), to control actions and enhance traffic control. This method simplifies administration tasks and can protect from unwanted traffic passing from one network to another. In addition to firewall, it is possible to use an access control list to filter switch ingress packets by the IP address, allowing network administrators to secure networks by controlling access to devices or the network parts.
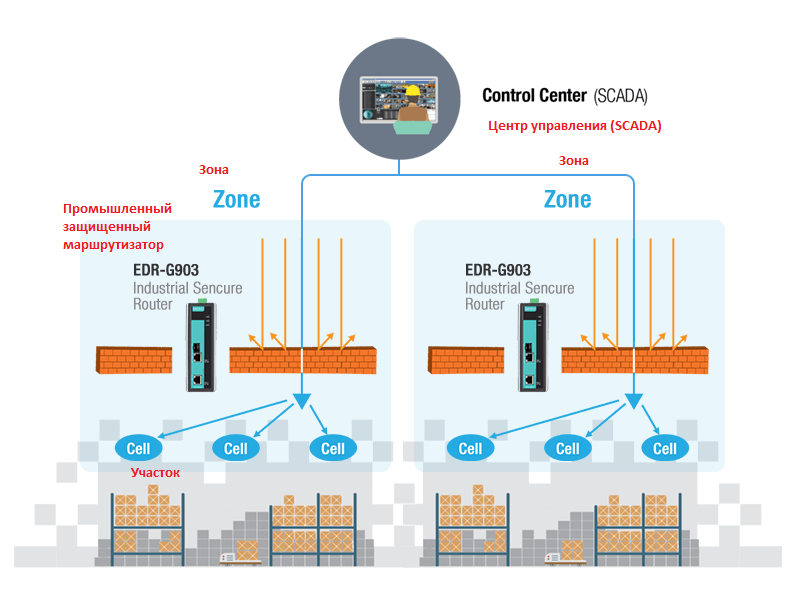
Define, what traffic can pass between the network zones.
Secure remote access to the enterprise network
Today, there are two solutions for secure remote access available. For constant connection, standard VPN tunnels are recommended. EDR series from Moxa can utilize IPsec, L2TP over IPsec or OpenVPN to configure encrypted IPsec VPN tunnels or OpenVPN clients. These methods protect data from being altered during transmission and provide secure remote access between industrial networks and remote applications. Alternatively, providing the remote access is required to be available on demand to specific computers or sensitive areas only, then a management platform for all remote connections is necessary.
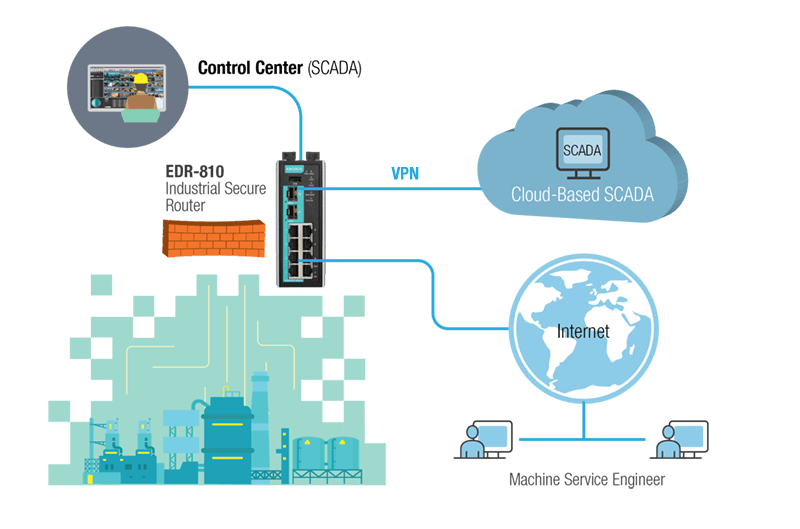
Remote access to the enterprise network.
MOXA solutions
Comfortable secure network management
The devices have protection features, but how to make sure that they are se t up correctly?
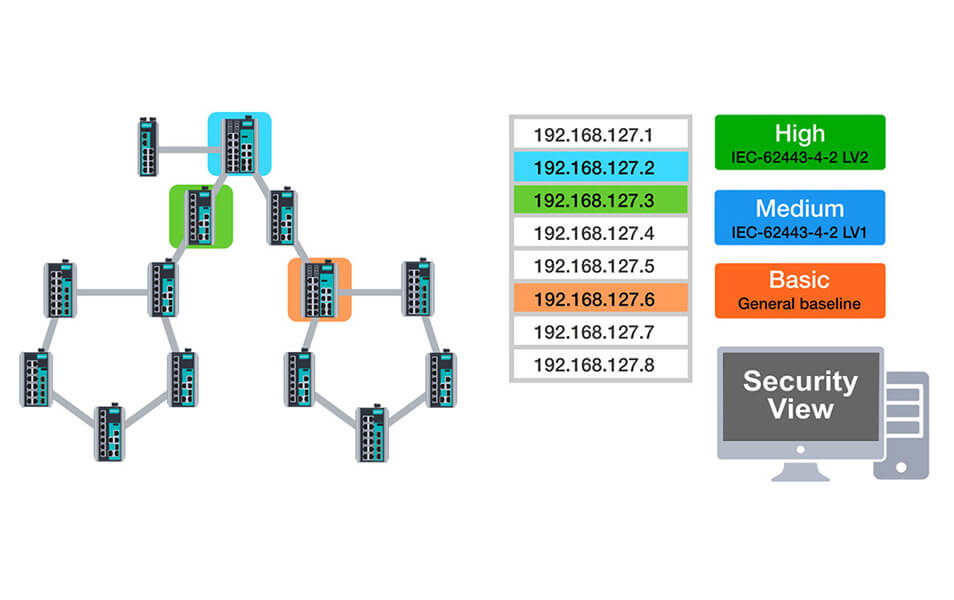
MXview network management system represents an integrated management platform that can manage network devices and monitor network condition directly from a web browser both locally, and remotely. Moreover, Security View function helps users visualize the security status of network devices. By using Security View, network administrators can view the security level of a device and check the security parameters such as the password policy status in real time for each network device. Users can apply built-in profiles that comply with the technical security requirements of the IEC 62443 standard. Security View also provides security experts the opportunity to create profiles. Network administrators can easily obtain a complete overview of the network security level and quickly respond to any vulnerability detected in their networks.
Save time on security management with MXconfig
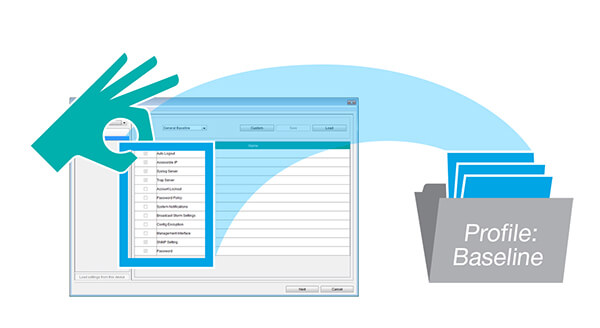
There are several security settings for each network device that should be checked and activated, in order to conform to the IEC 62443 technical standard requirements. Without such tools as MXview and MXconfig, network administrators have to check network devices manually one by one, in order to set the parameter, which requires much time and increases the error probability. MXconfig security wizard reduces setup time significantly, thanks to the simultaneous setting of large number of devices, and helps when configuring each device separately.
Application examples
With over 30 years of expertise in the sphere of industrial networks, Moxa utilizes its experience to help clients build secure networks by offering protection for PLCs, SCADA systems, factory networks, and remote access. Download the subject studies to learn more.

PLC and SCADA protection
Customer: Oil and gas service company
Task
High-capacity oil and gas pipelines often span thousands of kilometers. The pump stations along the pipeline are equipped with analyzers and PLCs. The customer found it complicated to maintain a secure and stable network connection between the stations and the remote SCADA system because the PLCs and I/O devices did not have any security features.

Factory networks protection
Customer: Automotive parts plant
Task
The manager of an automotive parts plant planned to digitalize all production processes. The field devices work on the EtherNet/IP protocol for control unification and data acquisition. As there is a large-scale network infrastructure in this plant, it is very complicated for the plant manager to monitor all devices and visualize the network topology. Moreover, in order to arrange the digitization, all networks must be interconnected from the field site to the ERP and to the cloud. It is crucial to have proper cybersecurity measures to allow the process of digitalization to occur without affecting production efficiency.

Remote access protection
Customer: CNC machine manufacturer
Task
Maximum network failure-free time increases the plant productivity. A leading manufacturer of mechanical power presses was to provide a prompt and more efficient after-sales service, in order to ensure enhanced machine performance and effective troubleshooting. At first, the manufacturer applied Windows-based Remote Desktop Control (RDC) technology, but, in this case, security risks and additional costs occurred. Moreover, a Windows-based computer is subject to security risks by itself, and the possibility of attacks becomes even greater when the computer gets connected to the Internet.
Why MOXA
In-depth approach to security
Moxa’s product portfolio is based on the in-depth defense concept that includes secure devices, secure network infrastructure, and security management.

Continuously enhancing security
Moxa follows a proactive approach to defend our products from vulnerabilities and help our customers manage security risks better.
Development of security systems for IT and OT
Moxa has entered into a partnership agreement with Trend Micro, in order to meet to the growing security demands as well as the security requirements from IT personnel.