
Table of contents:
Recently, search engines are reporting increase in the number of queries on cybersecurity. And this is not just a popular topic, but also a big issue for companies that are moving into the era of Industry 4.0 and the Industrial Internet of Things IIoT. According to Deloitte research, 4 out of 10 companies have experienced various information security incidents, and 86% of them noted a disruption of production operations. The trend towards the digitalization of manufacturing and the integration of OT manufacturing processes with IT information systems may increase the number of unsecured devices, which will open new ways for attackers to attack. In this article, MOXA experts provide some cyber security tips that will increase your company's security and help reduce the damage from cyber-attacks.
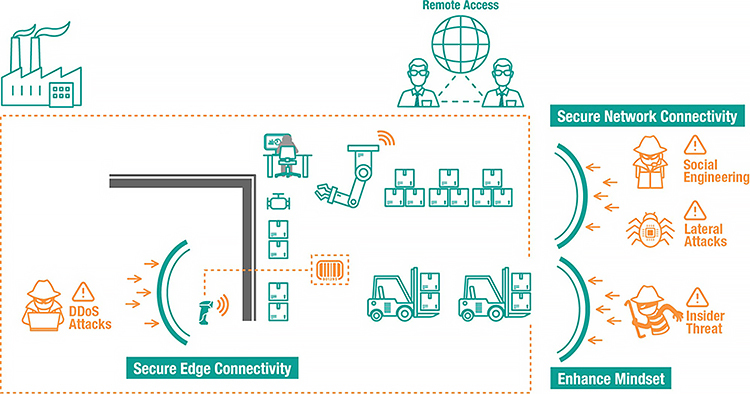
Create a network of devices with built-in security systems
Typically, industrial facilities use outdated equipment that has already been functioning for a long time, and now it has become vulnerable to cyber-attacks. Ideally, this problem could be solved by the complete replacement of obsolete equipment, but in real life, companies are faced with the inability to stop their processes, also they often don’t have a huge budget for modernization. Then one of the solutions to the problem may be to connect legacy equipment through network devices with built-in protection functions in accordance with the IEC 62443 standard.In addition, experts recommend the following course of actions:
- Change default password
- Disable unused ports and features
- Check Firmware Source Before Updating Devices
- Use secure protocols such as HTTPS
- Allow access to devices only to authorized users
- Encrypt critical data before sending
- Scan the network for potential security threats
- Update firmware to protect against network attacks
- Use virtual patching when unable to update hardware
Divide the network into multiple segments
Experts recommend dividing the network into segments to reduce the risk of blocking the entire network when an attacker gains access to one of the devices. Some users know that it is necessary to put a firewall between OT workflow networks and IT information systems, but in practice, most users do not do this. In addition, a regular firewall cannot detect industrial OT protocols. In this case, MOXA experts recommend using industrial firewalls, which not only allow you to segment the network, but also have the function of deep packet analysis to filter unauthorized access.
Use secure communications when transferring data
The main feature of integrating OT and IT is collecting raw data and converting it into useful form of information that can improve business efficiency and bring additional profit. To achieve this, cloud technologies with powerful tools for data analysis can be used. To securely transfer data to the cloud, you need to use secure communications. For example, data transmission via the OPC UA protocol allows for user authentication and authorization, and also satisfies the basic principles of information protection: confidentiality, integrity, and availability. In addition, it is worth using data encryption and VPN to secure critical assets.
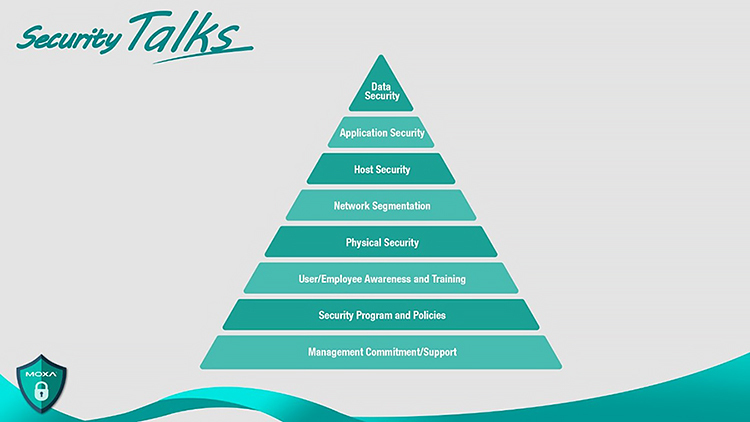
Raise cybersecurity awareness of all employees
Industrial cybersecurity awareness consists of several levels, which can be represented as a pyramid. The implementation and maintenance of safety rules by management form the base of the pyramid, followed by safety programs and policies, and awareness training for the organization's employees. Security policies determine who has access to read and write data in the system, but even the presence of such policies does not guarantee 100% adherence to them, because. employees may feel uncomfortable following them and fail to comply with them, leading to potential security risks. The management must constantly communicate to their employees the various safety rules and monitor their implementation in order to protect the entire system.
Check the hardware settings for compliance with the security policy
Perform a risk assessment and prioritize the protection of critical assets. The most important objects must be protected not only from the outside, but also from the inside. To do this, check the hardware settings for compliance with the organization's security policies and update them if necessary. Cyber security is a complex and multi-stage process, but even a few practical tips from MOXA experts will help you reduce the risks of cyber-attacks and protect the system as a whole.
For further technical information, inquiries about offers or placement of orders, please contact our sales team at sales@ipc2u.com

