
In the era of digital transformation, industrial data networks must be more reliable and secure than ever before. Moreover, evolving requirements for communication devices are forcing companies in various industries to modernize their infrastructure. While some are already implementing modern solutions with new communication protocols, most must modernize existing systems. Serial communication, which has long been the foundation of industrial automation, remains critical for integrating legacy systems with modern digital technologies. Secure and reliable serial communication solutions are especially important for industries such as energy, oil and gas, transportation, and manufacturing.
To meet the emerging challenges in today's industries, a new serial communications standard based on three principles is needed:
- Durability
- Adaptability
- Cybersecurity
In order to meet these principles and effectively solve modern problems, MOXA has developed a new series of serial device servers NPort 6000-G2, combining high reliability, advanced cyber protection features and improved performance characteristics.
Why do industrial applications prefer serial communication?
Industrial systems are designed for longevity and consistent performance. Unlike rapidly changing consumer technologies, industrial equipment typically lasts 5 to 15 years or more. Serial communications (RS-232/422/485) remain important due to its simplicity, flexibility, and cost-effectiveness..
Three key benefits of serial communication:
- Easy connection of multiple components.
- Scalability and minimal cabling costs over long distances (up to 1200 m using RS-485).
- Economical and easy to integrate, reducing overall operating costs.
Despite these advantages, serial communication still remains a bottleneck in terms of cybersecurity. Many manufacturers of serial converter devices neglected this point until the last moment, but not MOXA. The new generation surpasses the G1 in many characteristics, which will be discussed below.
Runs on Zephyr RTOS

To begin with, the new serial interface servers run on the Zephyr RTOS real-time operating system, which was built taking into account the 62443 standard and supports many features that provide protection against hacking. The open source code of the system allows you to quickly respond to emerging threats and promptly release updates, maintaining the relevance and security of the equipment throughout its entire service life.
Secure boot
Secure Boot is a mechanism that ensures that the device is started only with trusted, unmodified firmware. It is included in the list of mandatory measures to ensure trusted boot of IEC 62443-4-2 components (SL2 and above).
How does it work?
- The root certificate is embedded into the Nport ROM during hardware manufacturing. This key is written into memory that cannot be rewritten, so it cannot be changed.
- Each firmware is signed with a private MOXA key. Before the firmware is loaded onto the device, it is cryptographically signed.
- When the device is started, the bootloader reads the firmware and verifies its authenticity using the previously recorded public key:
- If the signature matches, the download continues;
- If it does not, the device does not run suspicious firmware.
- Even if an attacker gains physical access to the device and tries to upload malicious firmware via the debug interface, Secure boot will not allow it to start without a valid signature.
Authentication and access control
The RBAC (Role-Based Access Control) allows you to fine-tune user rights to interact with the device (divided into groups). This is a key measure for protecting against internal and external threats, especially in distributed and multi-user infrastructures. Thanks to this feature, you can create several users and configure each one with access to certain actions (only read or write settings, access to logs and diagnostics, the right to reboot or update firmware, etc.). The user connects to Nport via a secure channel, via HTTPS or SSH, and then performs actions according to access.
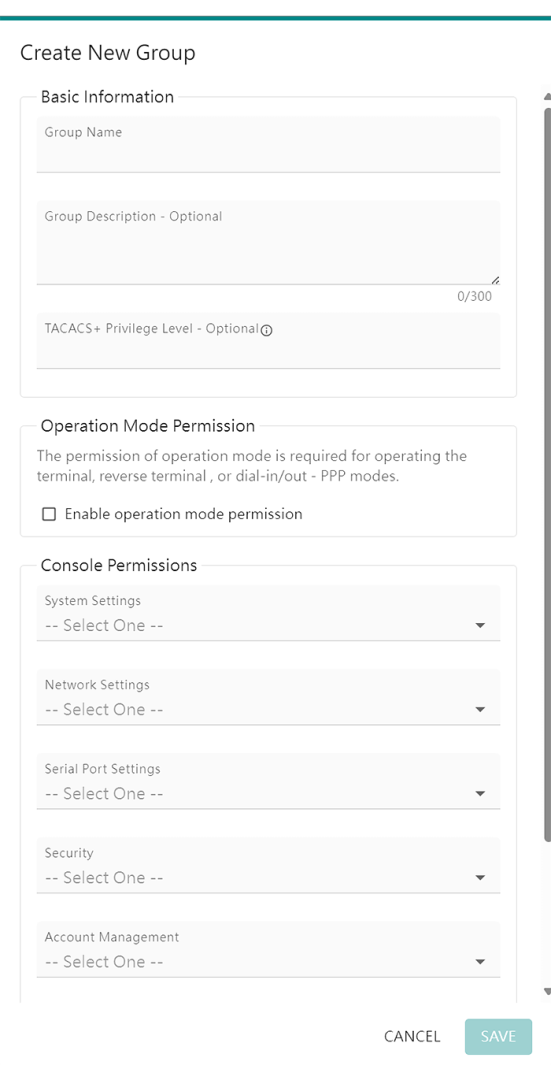
Instead of the default login and password, the user now needs to create a user during initial setup and set a secure password that meets the requirements of the 62443 standard (minimum length = 8, one digit required, lower and upper case, at least one special character).
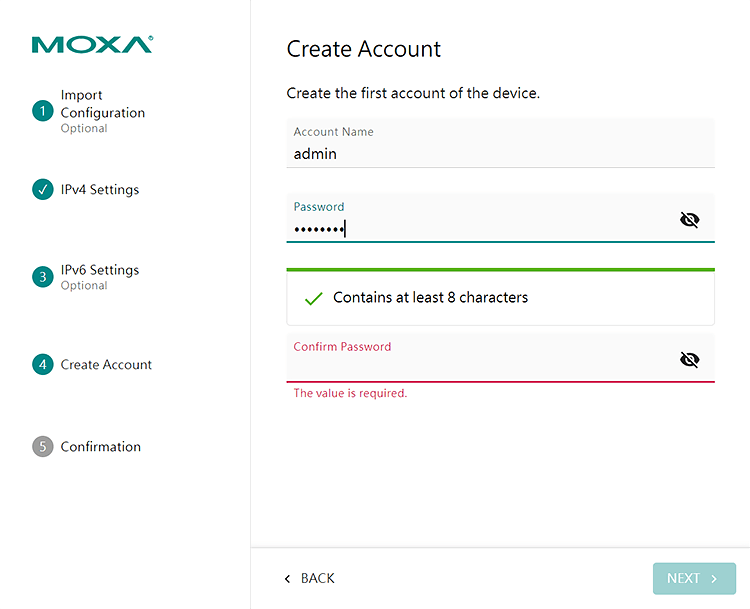
For organizations with a large number of devices and centralized access control policies, the ability to integrate with external authentication servers is critical. The NPort 6000-G2 Series supports two industrial protocols: RADIUS and TACACS+.
How it works:
- When a user connects, the device sends an authorization request to an external server (usually a domain controller or authentication server);
- The server returns permission or refusal, as well as the associated user role;
- Local settings are minimal: it is enough to specify the server IP, port and shared key.
Encryption of COM and Ethernet channels
Modern cyber threats often target data interception on the fly, especially in segments that use legacy or open communication between devices. To eliminate the risks of sniffing, spoofing, and man-in-the-middle (MITM) attacks, MOXA implements deep channel protection.
What exactly has been implemented?
- TLS/SSL/HTTPS for management: web interface, SNMP, Telnet and other network services can be configured to work over secure protocols.
- Encrypting traffic over serial ports: a mechanism for additional packaging and encryption of data transmitted between two points (Serial ↔ Ethernet) is used.
- Support for modern cryptographic algorithms:
- RSA up to 4096 bits (high security level).
- ECC (Elliptic Curve) up to 521 bits, equivalent to RSA 15360 - however, ECC is more efficient on resource-constrained devices.
Protecting console messages in out-of-band access
Out-of-band (OOB) is the management of devices outside the main production network, for example, via a separate RS-232 port. Although such a channel is considered secure by its architecture, in the context of real threats it becomes vulnerable if it is not encrypted.
Implementation in NPort 6000-G2:
- Console access can be protected by encryption and message authentication;
- Authentication and encryption occur even when connecting to a terminal port to eliminate MITM in an infrastructure with OOB network access;
- Access control and logging logic (syslog) also works in this channel.
Why is this important?
- The OOB interface is often used to restore the system in case of failures - a compromise can deprive the administrator of this ability;
- A secure OOB means that even if the main network fails, the attacker will not gain access to the device management.
Syslog and remote auditing (SIEM integration)
Security event logging is critical for attack detection, investigations and compliance.
Implementation features:
- Support for the standard syslog protocol according to RFC3164: this allows the device to be integrated with any monitoring system, such as Splunk, Graylog, ELK or IBM QRadar;
- Transfer of logs to a remote server: all key events (login, configuration changes, errors, access attempts, etc.) are recorded and can be sent in real time;
- Support for filtering and prioritizing events.
Why is it important?
- Quickly identify unauthorized activity;
- Compliance with corporate information security control requirements;
- Storing events outside the device - even if it is turned off or destroyed, the logs will be preserved.
MXview One Security View - monitoring the security status of devices
MXview One is an industrial network management system from Moxa, designed for visual monitoring and administration of network infrastructure. Within this platform, the Security View module is implemented, providing centralized management and control of the security status of devices, including NPort 6000-G2.

What does Security View do?
- Diagnosing vulnerabilities in configuration:
- Shows which device parameters do not meet security requirements (e.g. Telnet is open, there is no RBAC, weak password).
- Highlights potentially unsafe devices in the topology.
- Assessment of compliance with safety standards:
- Applies configuration checklists according to IEC 62443.
- Displays color status indication: "Safe", "Recommended to change", "Threat".
- Trend analysis and reports:
- Supports export of infrastructure security level reports.
- Helps to pass internal and external audits (for example, during ISO/IEC certification).
- Integration with other MXview modules:
- Security is about the topology and state of the network: you can see how a compromised device affects the rest of the system.
Fine-grained control of enabling/disabling functions and ports
During the setup process, the administrator can disable unused functions and ports: DNS_wins, SNMP agent, RIPD_PORT, HTTPS server, RADIUS, TACACS+, DHCP client, SNTP and others. This approach allows you to minimize the area of a potential attack (attack surface) due to the principle of minimum necessary functionality. In industrial conditions, where many network services are not used or are used only in limited areas, disabling unnecessary functionality reduces the risk of external penetration and makes the system more predictable in behavior.
In addition, each parameter can be enabled / disabled via the web interface, CLI or centrally via MXview One. This gives operators the ability to quickly respond to changes in security policy or infrastructure without having to reboot the device or reflash it.
This level of flexibility is especially valuable for network segmentation (for example, according to the IEC 62443 zone and channel model), where it is important to strictly control access to services from different trust levels.
Two ways of mounting
- Front mounting is the classic method on a DIN rail.
- Side mounting is convenient for compact cabinets and ones with limited depth.
Comparison with previous generations
|
|
NPort 5000/5000A |
NPort 6000 |
NPort 6000-G2 |
|
User profile |
Device security for small/medium businesses |
System security for enterprises |
|
|
Hardware Platform |
Standard element base |
|
|
|
Managing security policies |
|
|
|
|
Security protocols |
|
|
|
|
Integration into corporate systems |
No |
|
|
|
IEC 62443 compliance |
Support for IEC 62443-4-2 FR |
Developed according to the Secure by Design principle IEC 62443-4-2, level SL2 (certification in progress) |
|
|
Vulnerability maintenance |
Constant, performance limitations may apply |
Ongoing maintenance with the ability to update and expand protection |
|
Currently, 4 models are in mass production:
|
Model name |
RS-232/422/485 ports |
Secure Boot |
SD for buffering data from COM ports |
Operational temperature |
|
1 |
v |
- |
-10 to 60°C |
|
|
1 |
v |
- |
-40 to75°C |
|
|
2 |
v |
v |
-10 to 60°C |
|
|
2 |
v |
v |
-40 to 75°C |
Models from 4 to 32 RS-232/422/485 ports will be launched in November 2025. Stay tuned to our website for updates.

